Our Services / IT Security Solutions
Your Team of Security Experts
Cyber Security Advisors
Security is constantly evolving and should be top of mind for organizations. Our team of security experts including Certified Ethical Hackers and CISSPs are here for you. Cyber Advisors security solutions are straight to the point and enable your business to be more secure, protect your reputation and build awareness. They use multiple layers of security from only the top partners vetted by our security engineers within our labs.
Competitive Advantages
- Cyber Advisors is SOC 2 certified
- Cyber Advisors is an approved Registered Provider Organization (RPO) under the Cybersecurity Maturity Model Certification (CMMC) which regulates cybersecurity preparedness across the federal government’s defense industrial base (DIB)
- Cyber Advisors is recognized as a CRN Top 100 Security Provider
- Not only are we your security partner, Cyber Advisors goes beyond and are experts in total cloud infrastructure
- We believe in the human side of IT – Our team builds personal relationships, knows your business and is here for you
- Strategic security and technology roadmaps help to align your business and IT objectives
SECURITY DISCIPLINES
- External Reconnaissance
- External Vulnerability & Penetration Testing
- Internal Vulnerability & Penetration Testing
- Physical Security Assessment
- Web Application Penetration Testing
- Wireless Security Assessment
- Assumed Breach Assessment
- Firewall Assessment
- Active Directory Assessment
- Social Engineering Assessment (Phishing)
- Social Engineering Assessment (Pretexting)
- Incident Response Tabletop Exercise
- Digital Forensics & Incident Response (DFIR)
- Security Control Review
Virtual CISO (vCISO)
Security Expertise & Guidance for Your Organization
The Cyber Advisors Virtual CISO (vCISO) service is designed to improve your security posture and build your information security program. Most organizations do not have the budget or resources to hire a full-time CISO, but the need for understanding risk and seeking guidance and vision is a priority. Our team arms your organization with top-level security experts who will confidently assist your organization in navigating the security landscape.
Security Liasion
- Designed for companies with low technology complexity
- Up to 3 Hours per month of remote security engineer assistance
- – Security threat information
- – Cyber insurance review
- – Vendor due diligence review
- – Consult on security platform selection
- Development of incident response plan (IRP)
- Act as first responder for incident response
- Setup initial security baseline for organization devices
- Maintain security baseline monthly
- Program term – 1 year or prorated to your current CA Managed Services contract

STRATEGY & VISION
The Cyber Advisors vCISO is a high-level security expert who helps your organization set the strategy and vision around information security. The vCISO knows your business and is your trusted advisor and partner.

PROACTIVE EXPERTS
Threats are constantly evolving in the security landscape and we are here to protect your data, your team and your organization. The vCISO brings their knowledge and expertise to proactively manage risk, improve your security posture and build your information security program.

CUSTOMIZED
The Cyber Advisors vCISO works with your team to review business threats, assess potential threats, calculate risk, start policy development and create a remediation plan. We strive to meet your needs and create a customized plan that fits your business needs
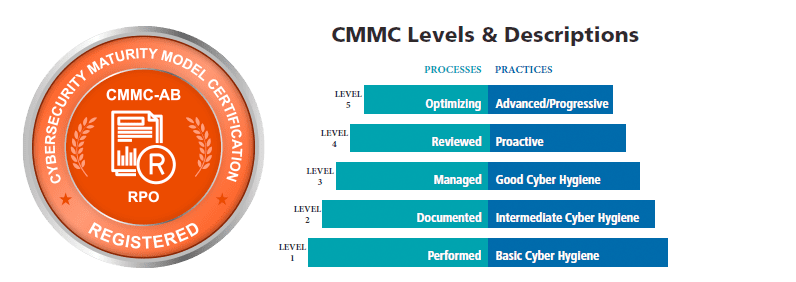
Approved Registered Provider Organization (RPO)
The Department of Defense is implementing the Cybersecurity Maturity Model Certification (CMMC) to regulate cybersecurity preparedness across the federal government’s defense industrial base (DIB).
Cyber Advisors is an approved Registered Provider Organization (RPO). The RPOs and RPs in the CMMC ecosystem provide advice, consulting, and recommendations to clients to help you navigate the CMMC. Cyber Advisors helps prepare our customers for CMMC readiness but does not conduct Certified CMMC assessments ourselves.
- Check out our blog on CMMC that dives into what you need to know, why it matters, the framework and 5 levels, and how to get started with Cyber Advisors: https://blog.cyberadvisors.com/cmmc
- Cyber Advisors CMMC marketplace profile: CMMC-AB | Cyber Advisors, Inc. | Marketplace
- Get started today: Cyber Advisors is a registered RPO and can assist your organization to prepare for the CMMC requirements – Please contact us today to speak to an RP by filling out the contact form
Executive Security Protection
Cyber Advisors Executive Security Protection (ESP) is transforming the security of executives and their families to better protect them from today’s society of increasing connectivity, creating ever-evolving cyber threats. ESP is a program for executives and their families and is intended to increase awareness of information security risks, protect their information, identities and assets. Cyber Advisors has developed this program to deliver a concise product while maintaining efficiency of time.
