Offensive Security
We put your tools and environments to the test - before attackers do.
Cyber Security & Penetration Testing Experts
Adversarial Simulation
Uncover organizational weaknesses through Red Team engagements, Purple Team engagements, social engineering, threat emulations, & threat hunting.
Application Security
We provide rigorous penetration testing of your mobile apps, web apps, & thick clients, as well as API security testing & application security code review.
Infrastructure Security
Identify critical network vulnerabilities through External/Internal Penetration Testing, PCI Penetration Testing, Wireless Penetration Testing, & Remote Access Penetration Testing.
Cloud Security
Assess & protect your cloud data, applications, & infrastructure in all cloud environments, including AWS, Google Cloud, & Microsoft Azure.
Device & IoT Security
Conduct comprehensive scans and assessments of devices with embedded software & IoT devices within your ecosystem to identify potential vulnerabilities & entry points for intrusions.
Offensive Strategy
Utilize the years of experience & deep industry knowledge of our expert team of security consultants for AppSec Program Management & Developer Security Training.
Adversarial Simulation
Uncover organizational weaknesses through Red Team, Purple Team, Social Engineering, Threat Emulation, & Threat Hunting.
Application Security
We provide rigorous penetration testing of your mobile apps, web apps, & thick clients, as well as API security testing & application security code review.
Cloud Security
Assess & protect your cloud data, applications, & infrastructure in all cloud environments, including AWS, Google Cloud, & Microsoft Azure.
Infrastructure Security
Identify critical network vulnerabilities through External/Internal Penetration Testing, PCI Penetration Testing, Wireless Penetration Testing, Cloud Security Assessment, & Remote Access Penetration Testing.
Device & IoT Security
Identify medical & embedded devices in an IoT-enabled environment & test critical hardware technologies to locate vulnerabilities & security-related issues.
Offensive Strategy
Utilize the years of experience & deep industry knowledge of our expert team of security consultants for AppSec Program Management & Developer Security Training.
How An In-Depth, Multi-Layered Penetration Testing Approach Works
Unlike other security firms, our Offensive Security Team extends our penetration testing protocols beyond the traditional means to provide in-depth, practical, & actionable insights through our unique three-phased Systematic Threat Evaluation Methodology (STEM).
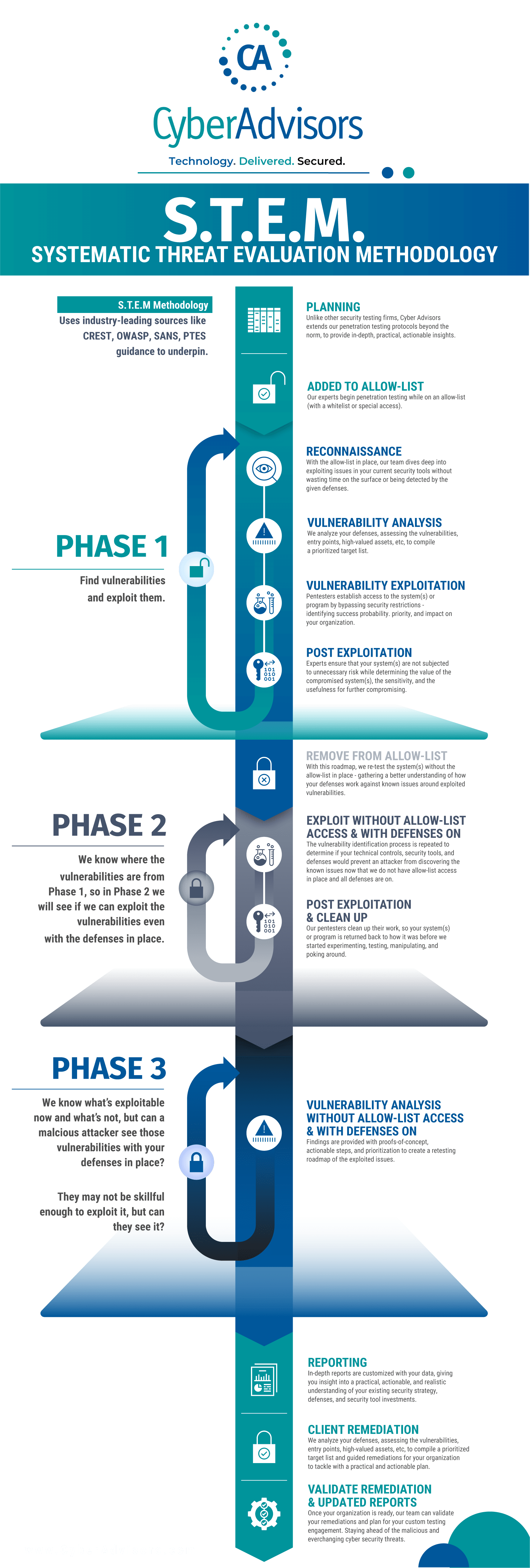
Work With Our Pentesting Experts

Prioritize Based On Risk Level
Address vulnerabilities based on your reality and not on a best-guess approach that relies on lab-based prioritization. Get real information from seasoned experts.

Compliance? Of Course, We Do That!
Professional compliance experts have you in mind, so you don't have to worry about checking boxes. We will provide comprehensive help to make sure that your next audit is a success.

Identify Areas For Improvement
Receive practical and actionable insights into your existing security strategy and security investments. Is your investment in preventative technologies safeguarding your business or does it need to be fine-tuned?

Gain In-Depth Results
Obtain a real-world understanding of the risks that identified vulnerabilities actually pose. Built on industry-leading security methods— our process delivers results.
Would You Like To Learn More About Our Offensive Security Services?
Learn From Our Offensive Security Experts Through Our Technical Blog

Obscurity Isn’t Security: A Practical Example
There is a saying in cybersecurity: “Obfuscation is not security”. In essen…

FortiGate SSL Inspection Tip: Fixing Self-Signed Certificate Blocks

Security Best Practices for Developers: Think Like a Hacker
General Security Advice for Developers As a pentester, development teams or…

