Compliance Audit Services
Get a holistic view of current risks and custom recommendations for quick remediation — before your next examiner's visit.
Verify your controls, expose potential risks, and protect community confidence.


Get the most accurate view of your security posture with a comprehensive assessment that goes well beyond just the technical.
Our IT Risk Assessment provides a panoramic view of risks that impact the information and data you rely on to operate. With specific remediation steps, you can quickly mitigate issues before they escalate, ensuring your operations remain uninterrupted and secure. By leveraging our process and expert guidance, you can create a resilient security framework that adapts to evolving risks and protects your most valuable assets.
Ensure your healthcare organization and patients are fully protected.
Attacks targeting healthcare entities and damaging patient data breaches are at an all-time high. With Cyber Advisor’s comprehensive HIPAA Security Risk Assessment, you can secure your day-to-day functions, your patients’ data and safety, and your community’s trust — all while ensuring regulatory compliance.


Discover hidden challenges in managing Protected Health Information (PHI) effectively and efficiently.
With health records of high value to patients and the dark web alike, Protected Health Information (PHI) is at risk for everything from unintentional employee mishandling to cyberattacks.
Our HIPAA Privacy Risk Assessment fully analyzes how you process, store, and transmit Protected Health Information, both physical and electronic.
We help you pinpoint potential problem areas with PHI and provide actionable remediation to quickly improve privacy practices and elevate your overall security posture.
This proactive examination ensures the integrity and security of sensitive health information, safeguarding your organization against potential breaches and compliance penalties.
Validate your policies and procedures for electronic funds transfers.
As required by the Federal Reserve, our FedLine Solutions Audit reviews your policies, procedures, and processes to prevent fraud, unauthorized access, or other unauthorized use of an electronic connection.
For any and all FedLine Solutiosn your institution utilizes, our prioritized remediation steps help you protect wire transfers, ACH, and most importantly, customer trust.


Avoid costly incidents by assessing distinct aspects of your policies and procedures to reduce costs and risk.
IT Asset Management improves cost efficiency and reduces risks by optimizing asset use and ensuring compliance. It enhances internal coordination with a centralized resource view and boosts efficiency through automation.
IT Project Management keeps projects on track and budget, identifying inefficiencies early to improve outcomes. It fosters collaboration with clear roles and timelines.
Vendor Management optimizes contracts and consolidates vendors to save costs and reduce risks. It also ensures smooth internal planning through clear communication and expectations.
Ensure your third-party partners are upholding the same security and privacy practices you expect from your own team.
As you extend your operations and collaborate with third-party partners, it’s critical to verify that these external entities adhere to stringent security and privacy protocols that match—or exceed—the standards you set within your own organization.
Our Vendor Management Risk Assessment reviews your processes and controls in place for validating that your TSPs are operating in a safe and sound manner across management, contracts, monitoring, SOC evaluations, and more.


Simulations are vital for delivering cybersecurity compliance and preparedness.
Tabletop exercises offer a controlled environment for teams to practice responses to potential incidents without real-life pressure.
By simulating scenarios, organizations can align their policies with regulatory standards and identify compliance gaps. These exercises also enhance overall preparedness, as staff from various departments can practice their roles, ensuring quick and effective action during a real attack.
Additionally, tabletop simulations promote continuous improvement by providing insights for refining strategies and staying ahead of emerging risks.
Types of Compliance Audits
IT General Controls Audit
Ensure the integrity of your organization by rigorously validating compliance. This process involves a thorough evaluation of your existing controls against the backdrop of the current risk landscape and the standards set by today's best practices.
By doing so, you not only safeguard your operations from potential vulnerabilities but also position your business at the forefront of industry excellence. This proactive approach to compliance ensures that your strategies are both effective and adaptive, ready to meet the challenges of the modern business environment head-on.
IT Risk Assessment
Gain comprehensive visibility into your entire risk landscape and swiftly address vulnerabilities to safeguard the critical systems and data that are fundamental to your operational success. Our advanced risk management solutions provide you with real-time analytics and insights, enabling you to detect and respond to potential threats with agility and precision. By leveraging cutting-edge technology and expert guidance, you can create a resilient security framework that adapts to evolving risks and protects your most valuable assets.
Staying one step ahead of potential threats is key.
By having a clear, panoramic view of your risk posture, you can identify and mitigate issues before they escalate, ensuring your operations remain uninterrupted and secure. Our integrated approach not only helps you uncover hidden vulnerabilities but also empowers you to implement proactive measures that fortify your defenses.
With our support, you can transform risk management from a reactive necessity into a strategic advantage, positioning your organization for sustained success in an increasingly complex threat landscape.
Ensure rigorous adherence to regulatory standards while safeguarding sensitive health information, preserving the integrity of critical healthcare operations, and, most importantly, prioritizing the welfare and safety of patients.
Now, when data breaches and cyber threats loom, our commitment extends beyond mere compliance; it's about building a fortress around the health data and systems that are vital to patient care and safety. Our comprehensive approach not only meets but exceeds industry standards, ensuring that every facet of patient information and operational functionality is protected.
By doing so, we maintain the highest level of trust and confidence in our ability to deliver safe, efficient, and reliable healthcare services.
Discover hidden challenges in managing Protected Health Information (PHI) effectively and efficiently. We can help you identify any lapses or vulnerabilities in your PHI handling processes.
With our expert analysis, you'll not only pinpoint these issues but also receive tailored recommendations for swift and effective remediation.
This proactive examination ensures the integrity and security of sensitive health information, safeguarding your organization against potential breaches and compliance penalties.
Safeguarding your assets and operations is paramount. Achieving this security through electronic funds transfers not only streamlines your transactions but also fortifies your defenses against potential threats.
Moreover, adhering to the stringent requirements set forth by the Federal Reserve is not just about compliance—it's about ensuring your transactions are conducted within a framework of trust and integrity. By embracing these standards, you are not only protecting your interests but also reinforcing the stability and reliability of your financial operations.
Ensuring the safety and confidentiality of your data is your top priority. As you extend your operations and collaborate with third-party partners, it’s critical to verify that these external entities adhere to stringent security and privacy protocols that match—or exceed—the standards you set within your own organization.
This not only protects your company’s valuable information but also fortifies the trust your customers place in your brand. By rigorously confirming that your third-party partners are committed to maintaining high levels of security and privacy, you are taking a proactive step in safeguarding your business against potential threats and vulnerabilities.
Assessing distinct aspects of your policies and procedures to reduce costs and risk, while elevating internal coordination and efficiency with:
- IT Asset Management
- Cost Reduction and Risk Mitigation: Optimizing IT asset management helps eliminate underutilized assets, cutting costs and reducing risks like security vulnerabilities and compliance issues. Proper tracking ensures all assets are updated and compliant, minimizing the chance of fines or breaches.
- Elevating Internal Coordination: Streamlined asset management improves communication between departments by providing a centralized view of resources, reducing redundancy, and ensuring everyone knows what tools are available.
- Boosting Efficiency: Automating asset tracking reduces manual tasks, speeding up decision-making and allowing the IT team to focus on strategic initiatives.
- IT Project Management
- Cost Reduction and Risk Mitigation: Effective project management ensures projects stay on time and within budget, reducing the risk of cost overruns and delays. Assessing current practices helps identify inefficiencies and potential risks early, leading to better project outcomes.
- Elevating Internal Coordination: Strong project management enhances collaboration, ensuring clear roles and timelines, which reduces miscommunication and aligns team efforts.
- Boosting Efficiency: Streamlined project processes improve resource use and task prioritization, leading to faster and more successful project delivery.
- Vendor Management
- Cost Reduction and Risk Mitigation: Optimizing vendor management allows for better contract negotiation, vendor consolidation, and elimination of redundancies, leading to cost savings and reduced risk from unreliable vendors.
- Elevating Internal Coordination: Effective vendor management ensures clear communication and expectations, helping internal teams plan and execute more smoothly.
- Boosting Efficiency: Streamlined vendor processes reduce administrative overhead and speed up procurement, allowing the focus to shift to strategic vendor relationships.
IT GENERAL CONTROLS AUDIT
IT RISK ASSESSMENT
Get eyes on your total risk posture and remediate issues quickly to protect the systems and data you rely on to operate.
HIPAA SECURITY RISK ASSESSMENT
Verify compliance while protecting health data, critical functions, and most importantly, patient safety.
HIPAA PRIVACY RISK ASSESSMENT
Uncover potential issues with Protected Health Information (PHI) handling and get recommendations for quick remediation.
FEDLINE SOLUTIONS AUDIT
Ensure security with electronic funds transfers and compliance with Federal Reserve requirements.
VENDOR MANAGEMENT RISK ASSESSMENT
Confirm third-party partners are upholding the same security and privacy practices you expect from your own team.
COMPLIANCE BEST PRACTICE EVALUATIONS
Assess distinct aspects of your policies and procedures to reduce costs and risk while elevating internal coordination and efficiency with these options:
Types of Tabletops
Incident Response
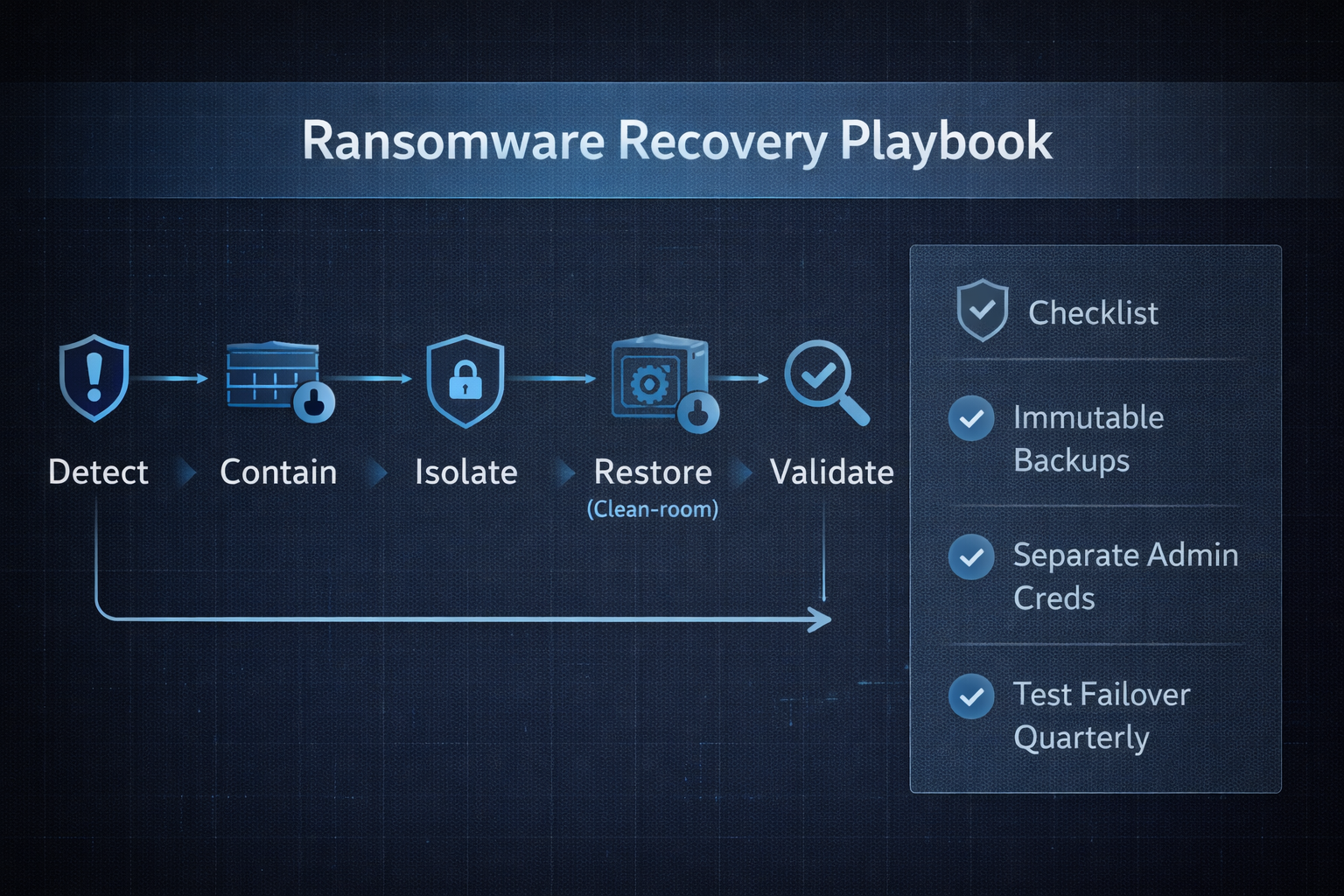
Test your organization’s readiness to quickly restore operations. We sequentially address six (6) major response areas to uncover gaps and provide recommendations for more effective incident handling.
Business Continuity
In a "no-fault" learning environment, identify gaps in policies and procedures for incident handling, internal coordination, and information sharing. Integrate learnings into emergency plans and operations.
Disaster Recovery
Identify operational gaps across eight (8) key recovery areas. Use custom recommendations to shore up your team's ability to effectively rebound from a real incident.
Our Blog
Stay up to date with what is new in the industry and learn more about upcoming events.
How VMware Strengthens Your IT Defense Strategy

Avoiding EDR Blind Spots on Laptops & Servers: Top 10

