.png?width=1584&height=396&name=CA%20and%20Fortinet%20(1).png)
Proud Fortinet Partner
Partnering with Fortinet
Secure Networking
Unified SASE
#1 Network Firewall Worldwide
Advanced Features
R&D Investment in 2023
Fortinet invested over $1B in research and development alone in 2023.
Fortinet Clients
Fortinet is the leader in physical storage, currently holding 32.7% of the total market.
Fortinet Next Gen Firewalls
99.98% Security effectiveness with perfect scores in 3 test scenarios
Fortify Your Network Through the Convergence of Networking & Security
Zero Trust Network Access (ZTNA)
Fortinet Universal ZTNA provides secure and simple access to applications, regardless where they are located, for users working from anywhere.
Secure Access Service Edge (SASE)
FortiSASE secures web, cloud, and app access for hybrid teams by uniting SD-WAN and cloud-delivered security service edge (SSE) in one platform.
Learn More
Next-Generation Firewall (NGFW)
FortiGate NGFWs accelerate security and networking performance to effectively secure the growing volume of data-rich traffic and cloud-based applications.
Learn More
Secure SD-WAN
Fortinet Secure SD-WAN delivers fast, reliable connectivity with built-in security; supporting cloud-first, security-sensitive, and global enterprises, as well as the hybrid workforce.
AI-Powered Security Services
FortiGuard AI-Powered Security Services is a suite of 20+ services that deliver real-time, layered protection against ransomware, malware, zero-day, and AI-driven threats across IT and OT environments.
Learn More
Security Operations Platform
The Fortinet SOC Platform enables security teams of any size to benefit from advanced detection, automation, and GenAI assistance to swiftly identify and respond to threats.
Learn More
Adversarial Simulation
Uncover organizational weaknesses through Red Team, Purple Team, Social Engineering, Threat Emulation, & Threat Hunting.
Application Security
We provide rigorous penetration testing of your mobile apps, web apps, & thick clients, as well as API security testing & application security code review.
Cloud Security
Assess & protect your cloud data, applications, & infrastructure in all cloud environments, including AWS, Google Cloud, & Microsoft Azure.
Infrastructure Security
Identify critical network vulnerabilities through External/Internal Penetration Testing, PCI Penetration Testing, Wireless Penetration Testing, Cloud Security Assessment, & Remote Access Penetration Testing.
Device & IoT Security
Identify medical & embedded devices in an IoT-enabled environment & test critical hardware technologies to locate vulnerabilities & security-related issues.
Offensive Strategy
Utilize the years of experience & deep industry knowledge of our expert team of security consultants for AppSec Program Management & Developer Security Training.
-3.png?width=2500&height=800&name=Untitled%20design%20(4)-3.png)
FortiSASE
FortiSASE integrates networking and security functions in a unified cloud-delivered service, providing consistent protection for users and data, regardless of location. This approach ensures secure, high-performance access to applications and resources, whether they are on-premises or in the cloud.
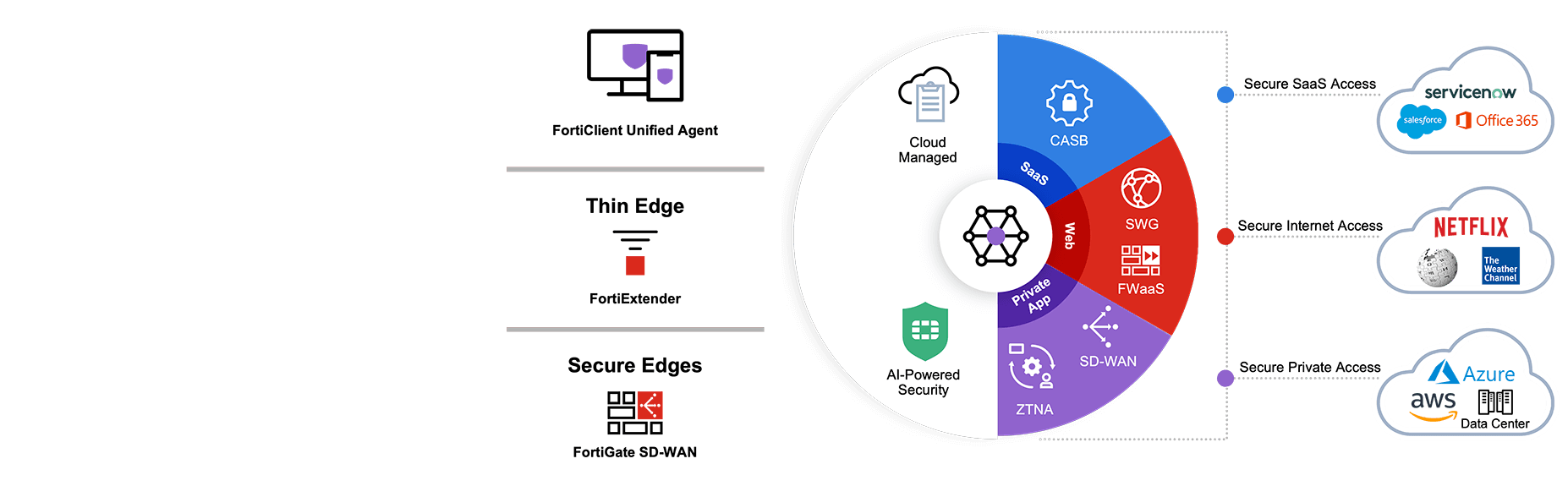
Secure SD-WAN
FortiGate delivers fast, scalable, and flexible Secure SD-WAN on-premises and in the cloud. Fortinet Secure SD-WAN supports cloud-first, security-sensitive, and global enterprises, as well as the hybrid workforce. Our Secure Networking approach uses one operating system and consolidates SD-WAN, next-generation firewall (NGFW), advanced routing, and ZTNA application gateway functions.
-3.png?width=2000&height=984&name=Untitled%20design%20(6)-3.png)
FortiGuard AI-Powered Security Services
A suite of 20+ services that are integrated across Fortinet’s security fabric and provides layered real-time and proactive protection against a broad range of threats including ransomware, malware, unknown, zero-day and AI-driven attacks across IT and OT networks protecting networks, files, content, Web traffic, SaaS deployments, Data, users, and critical infrastructure.
Fortinet SOC Platform
The Fortinet SOC Platform enables security teams of any size to benefit from advanced detection, automation, and GenAI assistance to swiftly identify and respond to threats. With flexible solutions tailored to both turnkey and advanced SOC operations backed by expert managed security services, Fortinet delivers solutions that meet the evolving needs of any organization.